That old server gathering dust in the storage closet? It's not just clutter. That stack of retired company laptops isn't just taking up space, either. They're ticking time bombs loaded with sensitive data.
Secure e-waste destruction is the critical process of making absolutely sure that data is permanently wiped clean before a device is recycled or discarded. It’s the only way to prevent catastrophic data breaches and stay on the right side of the law. Get this wrong, and you're exposing your organization to risks that can sink a business.
The Dual Dangers Lurking in Your Old Electronics
Every single retired electronic device is a potential liability. While many people think about the environmental side of e-waste, they often miss two far more immediate and costly threats: data breaches and compliance penalties. These aren't just abstract concepts; they are real-world dangers that have crippled companies that didn't take secure e-waste destruction seriously.
The sheer scale of the problem is mind-boggling. In 2022, the world generated an astonishing 62 million tonnes of e-waste. What’s truly alarming is that a massive 77.7% of it was completely unaccounted for. This mountain of discarded gear—much of it still packed with sensitive data—is a goldmine for cybercriminals.
Catastrophic Data Breaches from Discarded Devices
The moment a company phone, laptop, or server leaves your building without being professionally sanitized, you’ve lost all control over the information it holds. We're talking about everything from employee PII and client lists to your most guarded financial data and intellectual property.
Cybercriminals actively hunt for discarded electronics. They know that a single forgotten hard drive can be the key to your entire kingdom.
A breach that comes from improperly disposed e-waste is especially damaging. It screams to your customers, partners, and regulators that you were fundamentally careless with their information. The loss of trust can take years to rebuild, if ever.
Costly Compliance Failures and Legal Penalties
Beyond the nightmare of a data breach, the regulatory fines can be absolutely devastating. If you're in an industry governed by strict data privacy laws, you face non-negotiable rules for handling sensitive information—and that includes when a device is at the end of its life.
Just think about the implications here:
- Healthcare (HIPAA): A retired patient check-in tablet or an old hospital computer containing Protected Health Information (PHI) could trigger multi-million dollar fines if it’s found in a dumpster.
- Finance (GLBA/SOX): Old bank servers or employee laptops with financial records have to be destroyed according to very specific protocols to prevent fraud.
- Legal & Corporate (FACTA): Any business that handles consumer credit information is legally required to destroy that data securely before disposal.
The crucial takeaway is this: your legal responsibility for the data does not end when you unplug the device. It only ends when that data has been verifiably and permanently destroyed.
Skipping a formal, professional destruction process is a gamble you can't afford to take. The potential fines, legal battles, and reputational fallout far outweigh the investment in a secure disposal strategy. To learn more about finding the right partner, check out our guide on selecting a professional computer disposal company. This makes secure e-waste destruction an essential part of modern risk management.
Choosing The Right Data Destruction Method
Once you've sorted through your old equipment and flagged the assets that need secure data destruction, the next big question is how to do it. This isn't a one-size-fits-all situation. The best method really comes down to what you need to achieve—balancing total security, cost, and whether the device has any life left in it.
Making the wrong call here can be costly. You might spend too much on a level of destruction you don't need, or worse, you could choose a method that doesn't fully protect your sensitive data, leaving your organization exposed. It's like choosing a lock for a door; you wouldn't put a bank vault on a broom closet, but you also wouldn't secure your server room with a flimsy padlock.
Data Wiping For Asset Reuse
If you plan to reuse, resell, or donate your old tech, software-based data wiping is your best bet. This process, also known as sanitization, uses specialized software to systematically overwrite every bit of data on a hard drive with random characters. The gold standard here is the DoD 5220.22-M 3-pass wipe, which overwrites the data three times to make sure the original information is gone for good.
This is the perfect approach for routine IT hardware refreshes. Your laptops, desktops, and servers might be a few years old, but if they're still in good working order, data wiping allows you to capture their remaining value. The key is that the hard drive remains physically intact and fully functional.
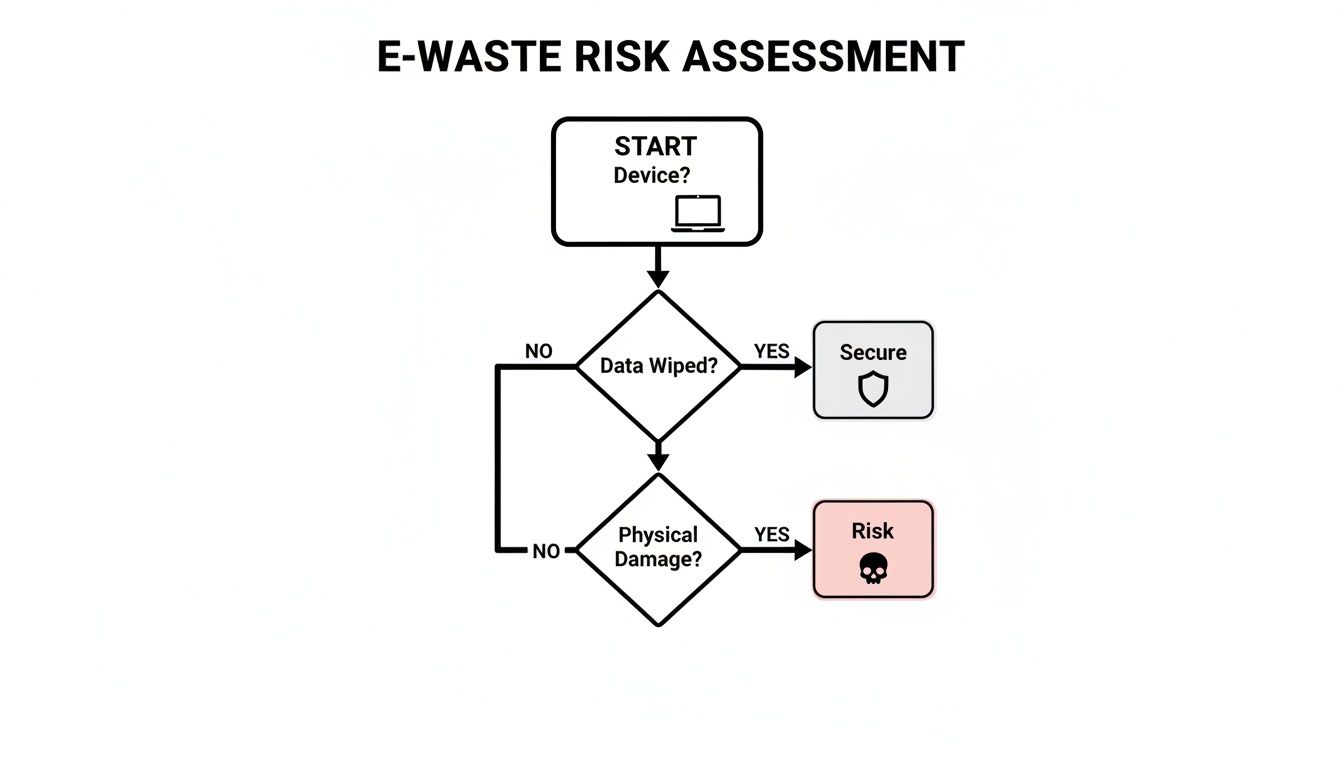
As this flowchart shows, the first question you must always ask is whether the data is secure. That single question separates a usable asset from a major liability.
Degaussing For High-Security Media
Sometimes, the data is so critical that the hard drive can never, ever be used again. For these scenarios, degaussing is the go-to method. A degausser is a beast of a machine that unleashes a powerful magnetic field, instantly and permanently scrambling the magnetic coating on hard drive platters or tapes where the data lives.
The process takes just a few seconds, but the result is irreversible—the drive is rendered completely useless. One critical thing to remember: degaussing does not work on Solid-State Drives (SSDs). SSDs use flash memory, which isn't magnetic, so the degausser has no effect. This technique is a common requirement for government agencies and defense contractors dealing with classified information.
For any organization handling top-secret R&D, sensitive financial records, or critical intellectual property, degaussing offers a certified guarantee that software wiping just can't provide. It’s the point of no return for data.
Physical Shredding: The Ultimate Failsafe
When you need absolute, 100% certainty that your data is destroyed beyond any possibility of recovery, nothing beats physical destruction. We’re talking about industrial-grade shredders that chew through hard drives, SSDs, smartphones, and tapes, grinding them into a pile of tiny, mangled fragments.
This is the most visually satisfying form of secure e waste destruction. There’s no question about whether the data is gone—you can hold the evidence in your hand. Shredding is the final answer for any device that is broken, at the end of its life, or held information so sensitive that you can't afford to take any chances. If you want a closer look at what this involves, our guide on the best ways to destroy a hard drive digs into the details.
The demand for these certified destruction methods is skyrocketing. The global ITAD (IT Asset Disposition) market, which focuses on secure erasure and asset recovery, is projected to hit an incredible $36.4 billion by 2034. This boom is being fueled by tough data privacy laws and increasing pressure on companies to manage their e-waste responsibly.
Comparing Data Destruction Methods
So, with these options on the table, how do you decide what's right for your equipment? This table breaks it down to help you match the method to your specific needs.
| Method | Security Level | Asset Reusability | Best For |
|---|---|---|---|
| Data Wiping | High | Fully Reusable | Reselling, donating, or redeploying functional IT assets with standard sensitive data. |
| Degaussing | Very High | Not Reusable | Destroying classified or top-secret data on magnetic media (HDDs, tapes). |
| Shredding | Absolute | Not Reusable | End-of-life, damaged, or SSD/flash media containing highly sensitive information. |
Ultimately, your choice comes down to a straightforward risk-versus-value calculation. If a device still has solid resale value and held standard business data, a DoD-compliant wipe is the smart, sustainable choice. But if that same device contains information that could ruin your company's reputation or finances if it ever got out, its resale value is zero. In that case, physical shredding isn't just an option—it's your only responsible choice.
On-Site vs. Off-Site Destruction Services
Okay, so you’ve figured out how you want your data destroyed. Now you have to decide where it happens. This choice is just as critical as the method itself, directly impacting your security, compliance, and even your budget.
This decision really comes down to two main options that professional vendors offer: they can bring the shredder to you, or you can send your old gear to their secure facility.

Understanding the practical differences between these two is key to building a secure e waste destruction plan that actually fits your organization. Each one has its place, depending on how sensitive your data is, what your logistics look like, and what you’re willing to spend.
The Airtight Security of On-Site Destruction
For organizations that can’t tolerate even a tiny risk in their chain of custody, on-site destruction is the gold standard. It’s exactly what it sounds like: a specialized mobile shredding truck pulls up to your location—whether that’s a corporate office, a humming data center, or a hospital. Your assets never leave your property until they are physically turned into tiny fragments.
The biggest benefit? You and your team can stand right there and watch the whole thing happen. This firsthand verification provides a level of transparency and peace of mind you just can’t get any other way. It completely eliminates the chance of a device getting lost, stolen, or otherwise compromised while in transit.
This approach is practically a requirement for organizations under strict compliance rules:
- Healthcare (HIPAA): A hospital can ensure patient PHI is destroyed without it ever leaving the campus, which makes audit trails incredibly straightforward.
- Finance (GLBA/SOX): Banks and investment firms can verifiably destroy drives containing sensitive financial data right on site, ticking a major regulatory box.
- Government & Defense: For agencies handling classified info, on-site destruction is often mandated to maintain absolute control over sensitive material.
The core advantage of on-site service is simple: no transit risk. By destroying assets before they’re ever moved, you maintain a perfect, unbroken, and observable chain of custody from beginning to end.
This is exactly why so many businesses look for local partners who can provide this hands-on service. For many companies in the Atlanta area, finding a vendor offering on-site hard drive destruction near me is a top priority, especially when they’re dealing with sensitive client or patient records.
The Practical Convenience of Off-Site Destruction
While on-site is unbeatable for security, off-site destruction offers a more streamlined—and often more cost-effective—alternative. In this scenario, a certified vendor picks up your palletized or containerized e-waste and transports it to their own secure, monitored facility for processing.
This is a great fit for businesses dealing with massive volumes of assets or those retiring equipment with less critical data. Think of a company refreshing hundreds of office PCs. Having a vendor handle all the logistics frees up your internal team to focus on their actual jobs.
Any reputable off-site partner will have security locked down from start to finish. You should expect:
- Secure, GPS-tracked vehicles for transport.
- Locked and sealed containers to prevent any tampering.
- A fully documented chain of custody, from the moment it leaves your dock to its final destruction.
Once the assets arrive at their facility, everything is inventoried and destroyed using the method you agreed on. Afterward, you’ll receive a serialized Certificate of Destruction, giving you the proof you need for compliance. This method is a smart blend of convenience and certified security, making it a go-to for routine IT asset retirement.
Ultimately, you have to weigh the absolute security of watching it happen yourself against the efficiency of letting the experts handle it off-site. Your answer will point you to the best fit for your organization.
How to Verify Your Data Is Actually Destroyed
Picking a destruction method is really only half the job. Without solid proof, your entire secure e waste destruction program is built on hope, not verification. This is where a rock-solid, documented chain of custody becomes your most important tool, turning a simple pickup into a defensible, auditable process.
This isn't just about shuffling papers around; it's your legal shield. If an auditor ever comes knocking or a breach is suspected, that audit trail proves you did your due diligence and took every responsible step to protect sensitive information from the moment it left your building.

The Anatomy of a Bulletproof Chain of Custody
A real chain of custody is an unbroken, chronological log of every single place an asset has been. It kicks off the second your vendor shows up and doesn’t wrap up until you have that final certificate in your hands. Anything less leaves gaping holes in your security.
A truly comprehensive process will always have these non-negotiable elements:
- Initial Asset Tagging: Before a single device is moved, each one needs to be scanned or tagged. This creates your starting inventory, matching serial numbers to your own internal asset list.
- Secure Transport Logs: If your gear is going off-site, the records must show it was loaded into a locked, sealed, and GPS-tracked vehicle. The log needs to have departure and arrival times noted.
- Serialized Inventory Reports: Once at the vendor’s facility, every asset is scanned again to confirm the whole lot made it. This report becomes the master list for the destruction phase.
This kind of step-by-step tracking makes it impossible for a device to "fall off the truck" or get lost before it's destroyed. It locks in accountability from beginning to end.
Decoding the Certificate of Destruction
The final, and most critical, piece of paper in this whole process is the Certificate of Destruction (CoD). Think of it as much more than a receipt—it's a legally binding statement confirming your devices were destroyed according to industry standards and data privacy laws.
A legitimate Certificate of Destruction is your ultimate proof of compliance. It should be detailed, serialized, and clearly link back to your initial inventory, providing an end-to-end audit trail for every single asset.
A flimsy or generic CoD isn't worth the paper it’s printed on. To make sure your documentation will hold up under the scrutiny of regulators or your own legal team, it has to have specific details. You can dive deeper into what makes a Certificate of Destruction a legally sound document in our detailed guide.
So, what should you be looking for?
- Unique Serial Number: The CoD itself needs a unique serial or reference number so it can be tracked.
- Detailed Asset List: It must list out every single device that was destroyed by its unique serial number. A vague count like "150 hard drives" just doesn't cut it.
- Method of Destruction: The document has to clearly state how the devices were destroyed (e.g., shredded to 2mm particle size, degaussed, DoD 3-pass wipe).
- Date and Location of Destruction: This confirms exactly when and where the destruction happened.
- Transfer of Custody Statement: This is the formal language that shifts liability from your organization to the vendor, confirming they’ve taken full responsibility for the assets.
Without these key pieces, you don't have the verifiable proof you need to defend your company's actions. To truly appreciate why this is so critical, it helps to understand the sophisticated data recovery methods that can pull information from devices you thought were wiped clean. That knowledge really drives home why verified, physical destruction and detailed reporting are so crucial. The CoD is your final proof that even the most advanced techniques would come up empty.
Selecting a Certified E-Waste Destruction Partner
Choosing your vendor is arguably the most critical decision in your entire e-waste strategy. This isn't just about finding someone to haul away old equipment; it's about selecting a security partner who becomes a direct extension of your compliance and risk management team.
Frankly, the wrong choice can expose you to the very data breaches and legal penalties you're trying to avoid. Differentiating between a basic recycler and a certified data destruction specialist is the first, most crucial step. A simple hauler might pick up your assets, but a true partner provides a defensible, auditable process that protects your business long after the equipment is gone.
Scrutinize Certifications That Matter
Certifications aren't just fancy badges to put on a website. They are hard-earned proof that a vendor adheres to rigorous, third-party audited standards for both security and environmental responsibility. But not all certifications are created equal, especially when we're talking about secure e-waste destruction.
Here are the credentials you absolutely must look for:
- NAID AAA Certification: Think of this as the gold standard for data destruction. It's non-negotiable. This certification means the vendor’s hiring practices, facility security, destruction processes, and even their insurance coverage have been thoroughly vetted by an independent security professional.
- R2v3 or e-Stewards: These certifications focus on the environmental side of things. They ensure your partner follows a strict hierarchy of reuse and recycling, properly manages hazardous materials, and maintains a documented downstream chain of custody for everything they process.
When you find a vendor with both a data-focused certification like NAID AAA and an environmental one like R2v3, you've found a partner that offers a complete, end-to-end solution. It's a clear signal they're committed to protecting both your sensitive data and the planet.
Asking the Tough Questions on Liability
Beyond certifications, you need to get into the weeds of the vendor’s liability coverage. A data breach from one of your discarded assets could easily run into the millions. You need ironclad assurance that your partner is adequately insured to handle that kind of catastrophic event.
A vendor’s insurance policy is a direct reflection of their confidence in their own security protocols. If they aren’t willing to invest in comprehensive coverage, you shouldn’t be willing to invest your trust in them.
As you vet potential partners, their commitment to broader information security standards is also telling. Ask about their internal protocols and whether they follow frameworks like the ISO 27001 certification process, a globally recognized benchmark for managing information security.
Your vetting process must include direct, pointed questions about their insurance. Don't be shy about asking for proof.
- Data Breach Insurance: Does their policy specifically cover data breaches that happen while your assets are in their custody? Insist on seeing the certificate of insurance and pay close attention to the coverage limits.
- Pollution Liability Insurance: This covers cleanup costs if an environmental incident happens. It’s a key indicator of a truly responsible recycling partner.
- General Liability: This is standard, but you should still verify that their coverage is sufficient for the scale of your operations.
If a vendor hesitates or pushes back when you ask for this documentation, that's a massive red flag. Transparency here isn't a bonus; it's a baseline requirement. This is especially true when contracting for specialized hard drive destruction services, where the risk is so heavily concentrated on data-bearing devices.
Vendor Vetting Checklist
To make this easier, I've put together a checklist you can use during your evaluation process. A thorough review using these points will help you confidently choose a partner who can provide genuinely secure e-waste destruction.
| Verification Item | Why It Matters | What to Ask For |
|---|---|---|
| NAID AAA Certification | Verifies adherence to the highest standards for secure data destruction, including employee screening and facility security. | A current copy of their NAID AAA certificate and confirmation that it covers on-site services if needed. |
| R2v3 or e-Stewards Certification | Confirms environmentally responsible recycling practices and a vetted downstream recycling chain. | Their official certification number, which you can verify on the respective organization's website. |
| Insurance Policies | Protects your organization from financial liability in the case of a data breach or environmental accident. | Certificates of Insurance for Data Breach, Pollution Liability, and General Liability coverage. |
| Downstream Partner Vetting | Ensures that any partners they use for final material processing also meet high security and environmental standards. | A description of their downstream vetting process and a list of their primary downstream partners. |
| Reporting & Audit Trail | Provides the serialized, legally defensible documentation you need for compliance and internal audits. | Sample copies of their Certificate of Destruction and serialized inventory reports. |
Taking the time to properly vet your vendor on the front end will save you from unimaginable headaches—and potential financial disaster—down the road. Do your homework, ask the hard questions, and choose a partner you can trust implicitly.
Common Questions About Secure E-Waste Destruction
Even with a solid plan, you're bound to have questions when you start putting a secure e-waste destruction program into action. Getting into the weeds of compliance, security, and proper verification can feel like a maze.
Let's clear up some of the most common questions we hear from Metro Atlanta organizations just like yours. A little expert insight can go a long way in making you feel confident that your data destruction process is as airtight as it needs to be.
Is Deleting Files or Formatting a Drive Enough?
Not even close. Honestly, this is one of the most dangerous misconceptions we see in data security.
When you hit 'delete' or format a hard drive, you're just removing the digital signposts that tell the operating system where to find the data. The actual information—all those ones and zeros making up your sensitive files—is still sitting right there on the drive. Anyone with easily accessible (and often free) recovery software can pull that "deleted" data back in a few hours.
Think of it like ripping the table of contents out of a book. The chapters are all still there; they're just a little harder to find at first. Real data security only happens when the information is rendered completely unrecoverable through professional methods like multipass data wiping, degaussing, or physical shredding.
What Is a Certificate of Destruction?
A Certificate of Destruction (CoD) is your official, legally recognized proof that your electronic assets were properly destroyed according to all relevant data privacy laws. It’s the final, crucial link in your audit trail and serves as a defensible record of your due diligence.
A proper CoD isn't just a receipt. It's a legal document that formally transfers liability and proves you took every necessary step to safeguard sensitive data. Without one, you have absolutely no verifiable evidence of proper disposal.
A legitimate certificate has to be detailed. It should include a unique serial number for the document itself, a full inventory of every destroyed asset (listed by its own serial number), the exact destruction method used, the date of destruction, and a clear statement confirming the transfer of custody.
Can We Get in Trouble for Our Vendor’s Mistakes?
Yes, you absolutely can. This point can't be stressed enough.
Under major data privacy regulations like HIPAA (for healthcare), GLBA (for finance), and FACTA, the ultimate responsibility for protecting data always stays with your organization—the original owner of that data. You simply cannot outsource your liability.
If the vendor you hire mishandles your assets and it leads to a data breach, your company is the one on the hook. That means facing massive regulatory fines, potential lawsuits, and devastating damage to your brand's reputation. This is exactly why vetting your partner and insisting on credentials like a NAID AAA Certification isn't just a good idea—it's an essential move to protect your business from someone else's costly mistakes.
At Montclair Crew Recycling, we give Metro Atlanta businesses the certified, transparent, and defensible data destruction services they need to eliminate risk and guarantee compliance. To build a secure e-waste program you can truly trust, learn more about our process.
