Yes, Apple has a recycling program, and it’s a pretty slick system for individuals looking to trade in an old device for some credit or just get it off their hands responsibly. Think of it as a consumer-first approach, designed for maximum simplicity when you're dealing with one iPhone, iPad, or Mac at a time.
What Is the Apple Recycle Program for Consumers?

Before we get into the nitty-gritty of what a business needs, it's worth understanding how Apple's program works for the average person. The entire system is built on two simple paths, both tailored for someone managing a handful of their own personal devices.
It’s a bit like returning a few glass bottles to the grocery store for a deposit. The process is easy, effective, and feels good on a small scale. It's just not built to handle a truckload of returns from a whole company.
The Two Pillars of Apple Recycling
Apple’s consumer program boils down to two main channels, each serving a different need for the device owner.
-
Apple Trade In: This is the one that puts money back in your pocket. If you’ve got a fairly recent iPhone, iPad, or MacBook, you can trade it in for an Apple Gift Card or a discount on your next purchase. The process is dead simple—you answer a few questions online about its condition, get a value estimate, and then either ship it off or drop it at an Apple Store.
-
Free Recycling: What about devices that are too old, broken, or just not eligible for a trade-in? For those, Apple offers a completely free recycling service. This ensures the product is taken apart correctly and its materials are recovered instead of it just ending up in a landfill.
This one-two punch makes it incredibly easy for any individual to do the right thing with their old electronics. It’s a clean, user-friendly system that backs up Apple’s big talk on environmental responsibility.
The whole consumer-centric model is a cornerstone of Apple's green strategy. It gives individuals a clear path to make sure their old tech is either reused or broken down for its raw materials.
And they’ve taken this model global in a big way. Apple's take-back and recycling efforts now cover 99% of the countries where they sell products, which is a massive footprint.
How the Process Works for Individuals
The entire system is designed for convenience. Someone wanting to get rid of an old iPhone can kick off the whole process online in a couple of minutes. Apple sends a prepaid shipping box or gives instructions for an in-store drop-off, making it almost zero effort for the user.
This is where the line between personal and business needs becomes crystal clear. The system assumes a single user is handling their own data wipe and is motivated by a gift card or a sense of personal duty. That’s a fantastic solution for one person, but it starts to fall apart fast when you try to scale it up—a problem we'll dig into next.
If you want to know more about the basics of phone disposal, our guide on how to recycle mobile phones is a great place to start. This foundation helps explain exactly why businesses need something much more robust.
Why Apple’s Program Just Doesn't Work for Businesses
Let’s be clear: Apple's recycling program is fantastic for what it is. It’s designed for a single person trading in their old iPhone for a new one. It's simple, clean, and convenient. But what happens when your Atlanta business needs to retire 50 MacBooks after a company-wide upgrade? That streamlined process shatters into a logistical nightmare.
Think about it. Your IT manager can't just box everything up and send it off. Instead, they're stuck processing 50 individual trade-ins. Each machine has to be entered online, evaluated, packaged, and shipped separately. There's no bulk shipping, no business account manager, no single point of contact. The sheer administrative work makes it a non-starter for any company retiring more than a couple of devices at once.
Trying to use this program for a business is like catering a corporate lunch by sending every single employee through the drive-thru, one at a time. It’s painfully inefficient and completely out of sync with how a business needs to operate. The system simply wasn't built to handle corporate volume.
The Scale and Logistics Problem
The first wall you hit is volume. Apple’s program is a one-to-one transaction model. Businesses, on the other hand, manage entire fleets of devices. When you try to force a consumer process onto a corporate problem, the logistics immediately fall apart.
Here are the key hurdles you'll face:
- No Way to Process in Bulk: Every single device needs its own trade-in submission. If you have 50 devices, you have 50 separate transactions to create, manage, and track.
- No On-Site Services: Forget about a professional, secure pickup. The burden is entirely on your team to pack and ship every single asset, one by one.
- A Mess of Payouts: Any money you get back comes in the form of individual gift cards or credits. For a finance department, trying to reconcile dozens of small credits is a bookkeeping disaster.
This isn't just a minor inconvenience. It’s a fundamental design flaw that makes the program unworkable for most companies. Businesses need a coordinated, single-project solution, not a pile of disconnected consumer transactions.
The Massive Gap in Security and Documentation
Logistics are a headache, but this next part is a serious risk. The Apple program provides absolutely none of the documentation that businesses are required to maintain. When a company retires an IT asset, it's not just about getting rid of it; it's about proving you did it securely and in compliance with the law. This is where Apple's program completely misses the mark for business needs.
A business needs legally defensible proof that its data was destroyed and the equipment was handled correctly. Apple's program gives you none of it.
You will NOT receive any of these critical documents:
- Certificates of Data Destruction: There is no formal certificate to prove that your sensitive company and client data was properly destroyed according to industry standards like NIST 800-88.
- Serialized Asset Reports: You won't get a detailed inventory report listing every device by serial number. This leaves a huge hole in your audit trail for both compliance and internal asset tracking.
- Proof of Compliance: The program provides no paperwork to help you prove you’re meeting regulatory standards like HIPAA, PCI DSS, or SOX.
A simple email confirmation from a consumer trade-in program offers zero legal protection during a data breach investigation or a compliance audit. This lack of formal documentation creates an unacceptable level of liability.
Ultimately, Apple's program puts the entire responsibility for data security on you. It operates on an honor system—fine when you're wiping personal photos, but dangerously insufficient when you're dealing with protected corporate information. A real enterprise solution must provide certified, auditable proof every step of the way.
Apple's Program vs a Certified ITAD Partner
When your business needs to retire a fleet of Apple devices, you’re at a crossroads. It's a choice that goes way beyond just getting rid of old gear. On one side, you have the familiar recycle program Apple offers—a system designed, frankly, for individuals. On the other, you have a certified IT Asset Disposition (ITAD) partner, a specialist service built from the ground up for the complexities of business.
The difference isn't just about handling more devices; it's about entirely different goals. Apple’s program is a simple take-back service focused on consumer convenience. A certified ITAD partner, however, is there to manage the entire asset lifecycle for your company, focusing on four areas where the consumer model just can't keep up: logistics, data security, compliance, and getting the most value back.
The Logistics and Scale Divide
Trying to manage a corporate device refresh using Apple’s mail-in program is like trying to build a house with a single screwdriver. Sure, the tool is useful for a small job, but it's completely out of its league on a major project. That’s the gap between Apple’s program and an ITAD partner when it comes to business logistics.
An ITAD partner brings the right tools for the job. Instead of your team wrestling with dozens of individual mail-in kits and trips to the post office, a professional ITAD provider handles everything.
- On-Site and Secure Logistics: A trained, insured team comes to you. They securely pack and transport all your assets in one go.
- Chain of Custody Documentation: From the moment a device leaves your office, its journey is tracked and documented. This creates an unbroken, auditable trail.
- A Single, Coordinated Project: The whole process is managed as one cohesive project, not a hundred separate consumer transactions.
This professional approach cuts out the administrative headaches and hidden labor costs that come from trying to make a consumer program do a business’s job.
Using Apple's program for a corporate asset retirement of 50 MacBooks is like asking your finance department to process 50 separate, small invoices instead of one consolidated bill. It’s not just inefficient; it’s a waste of valuable internal resources.
For any business, picking the right service is critical. Taking a moment to understand what top-tier IT asset disposition companies actually do can help you make a smart decision that protects your organization.
Unpacking the Security and Compliance Gap
For any business, data security is non-negotiable. This is probably the single biggest difference between Apple’s program and a certified ITAD partner. Apple's process puts the entire responsibility for wiping data on you, the user. It’s a high-risk "honor system" that offers zero legal or regulatory protection for a business.
A certified ITAD partner works under a completely different model—one built on verification and proof.
This diagram breaks down the main business limitations you'll hit with consumer-grade recycling programs.
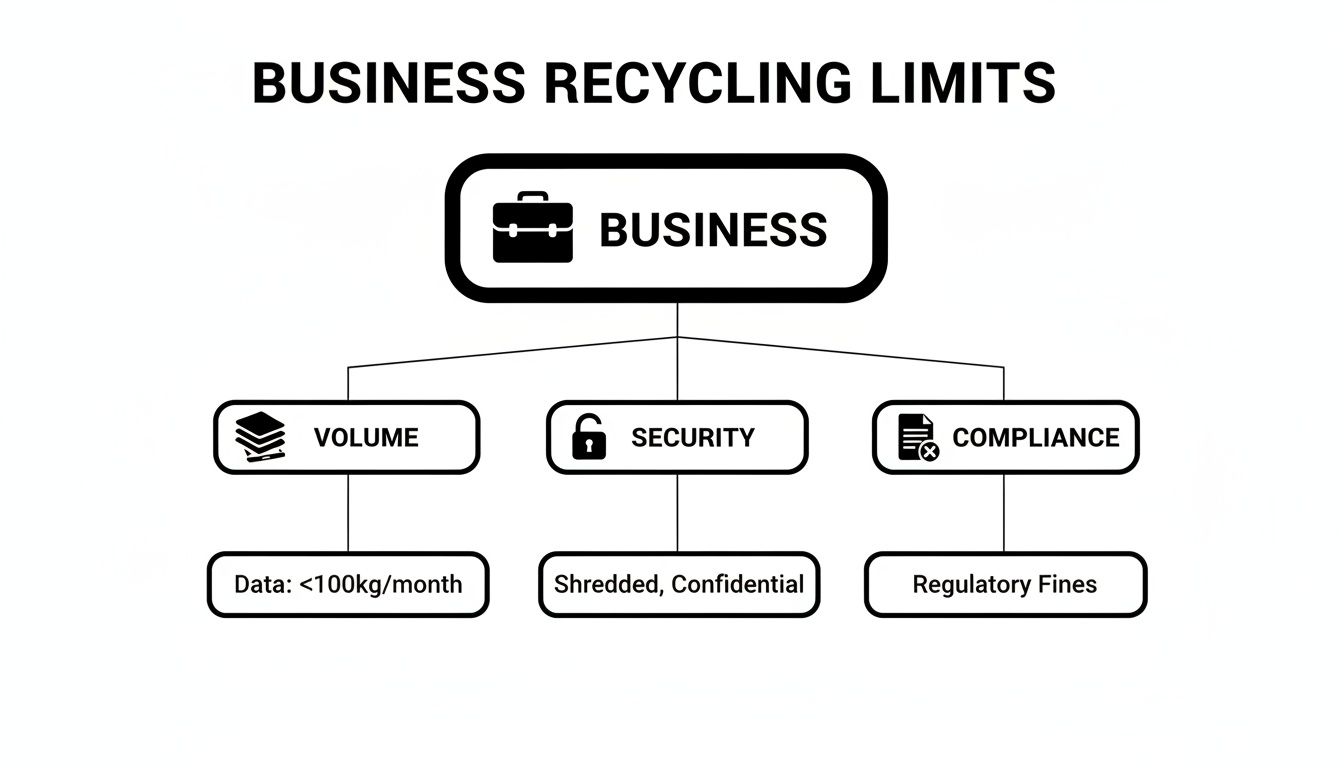
The image really shows how the demands of volume, security, and compliance create a service gap that only enterprise-level solutions can fill.
An ITAD specialist provides legally defensible services that a consumer program simply can't.
- Certified Data Destruction: They use processes that meet strict standards like DoD 5220.22-M or NIST 800-88 to sanitize your data.
- Certificates of Destruction: You get formal, serialized documents proving that the data on every single device was properly destroyed.
- Physical Destruction Options: For ultimate security, they can physically shred hard drives right at your location, giving you absolute certainty that the data is gone forever.
- Compliance Documentation: They provide detailed audit reports you need to prove compliance with regulations like HIPAA, PCI DSS, and SOX.
This certified, documented process turns data security from a huge liability into a verified, closed loop.
A Clear Comparison for Decision Makers
To put it all into perspective, let's look at a direct, side-by-side comparison. The table below really spells out why one is a consumer convenience and the other is a vital business service.
Apple Recycle Program vs Certified ITAD Partner
| Feature | Apple Recycle & Trade-In Program | Certified ITAD Partner |
|---|---|---|
| Bulk Processing | No, individual transactions only | Yes, handles entire fleets in one project |
| Logistics | Mail-in kits; user is responsible | Secure, on-site pickup and logistics |
| Data Destruction | User's responsibility | Certified, documented, and auditable |
| Certificate of Destruction | Not provided | Provided for every serialized asset |
| Asset Reporting | Basic trade-in confirmation | Detailed, serialized inventory reports |
| Compliance Support | None | Documentation for HIPAA, PCI DSS, SOX |
| Value Recovery | Limited to gift cards for eligible devices | Remarketing, refurbishment, and revenue sharing |
| Physical Security | Depends on public shipping | Secure chain of custody from start to finish |
This table makes the service gap crystal clear. While the recycle program Apple has created is a great environmental initiative for individuals, it just doesn't have the security, documentation, or logistics needed to protect a business from financial, legal, and reputational risk. For any organization in Metro Atlanta or beyond, partnering with a certified ITAD provider is the only choice that lines up with professional standards of security and compliance.
The Critical Data Security Gap Businesses Cannot Ignore

Beyond the logistical headaches, the biggest red flag with using a consumer-focused recycle program Apple offers is the enormous data security gap it creates for any business. For an organization, data isn't just information—it's a regulated, high-value asset that carries immense legal and financial weight. Failing to protect it during disposal isn't just a mistake; it's a major liability.
Apple's program runs on a very simple premise: you, the user, are completely responsible for erasing your data before sending a device in. It’s an “honor system,” assuming you've correctly wiped everything clean. While that might be fine for your personal photos and contacts, it’s an indefensible risk when corporate IP, client information, or employee records are on the line.
This approach leaves your business with zero proof that the data was ever truly destroyed. If a breach is ever traced back to one of your retired assets, "we thought we wiped it" offers no legal protection whatsoever.
The Honor System Is Not a Security Policy
Imagine a law firm in Atlanta retiring a dozen MacBooks. These devices hold sensitive case files, privileged client communications, and confidential financial records. Just running a factory reset and dropping them in a box for Apple is a catastrophic gamble.
A motivated person with the right software tools can often recover data from improperly wiped drives. That simple mistake could expose the firm and its clients to incredible risk. This is where the line between a consumer convenience and a true enterprise solution is drawn in the sand. A business can't build its compliance strategy on an honor system; it needs a verifiable, auditable, and legally defensible process.
Trusting employees to perfectly execute data wiping procedures on dozens of devices without certified verification is not a security strategy; it’s a compliance failure waiting to happen.
The entire burden lands on your internal team, who might not have the specific training to ensure data is truly irrecoverable. This creates a huge weak link in your security chain at the final stage of a device's life. To properly identify and plug these kinds of holes, businesses should consider professional cybersecurity risk assessment services to get an expert eye on their disposal protocols.
Certified Destruction The Only Defensible Method
Unlike Apple's hands-off model, a certified ITAD partner provides concrete, verifiable data destruction that slams this security gap shut. These aren't just suggestions; they are rigorous processes built to meet strict government and industry standards.
There are two primary methods that give businesses the absolute certainty they need:
-
Certified Data Wiping: This is way more than just deleting files. Specialists use software that follows standards like DoD 5220.22-M or NIST 800-88, which overwrites the entire drive with random data multiple times. This makes the original information impossible to get back. Most importantly, it generates a serialized Certificate of Data Destruction for your compliance records.
-
Physical Hard Drive Shredding: For the highest level of security, nothing beats physical destruction. A mobile shredding truck can come right to your office, letting you watch the hard drives from your old MacBooks and servers get turned into tiny, irrecoverable metal fragments.
These methods replace the risky honor system with absolute proof. This documentation is your shield during an audit or in the event of a security incident, proving you took every necessary step to protect sensitive information. When compliance with HIPAA, PCI DSS, or SOX is on the line, this verifiable proof is indispensable. Businesses looking for this level of security can find more details on certified IT asset destruction to see how these processes protect them from liability.
Maximizing Financial and Environmental Returns
Smartly handling your old IT assets is about much more than data security—it's a massive opportunity to hit your financial and environmental targets. Sure, the basic recycle program Apple offers is a decent starting point, but working with a certified ITAD partner turns a simple disposal task into a strategic advantage. It's how your company can build a genuine sustainability story while actually boosting your bottom line.
A certified partner makes sure every single component from your old Apple gear is handled for maximum value. We're talking about meticulously recovering materials like aluminum, copper, and rare earth elements so they can go right back into the manufacturing supply chain. This is the circular economy in action, cutting down on the need for new mining and shrinking your company's environmental footprint.
This isn't just theory; it has a real impact. Just look at Apple's own efforts.
Apple reported that recycled and renewable materials made up 24% of the mass of materials shipped in its products. On top of that, their suppliers kept about 600,000 metric tons of waste out of landfills. That shows you what a focused recycling strategy can really do.
Turning Disposal Costs into Revenue Streams
Beyond the green benefits, the financial upside of using a real ITAD partner is huge—and often completely missed. Apple’s trade-in program is incredibly picky. They typically only want recent, perfect-condition devices for credit. If you have anything older, slightly damaged, or specialized, you're usually out of luck.
This is where a certified partner gives you a clear financial edge. They have the know-how and the network to squeeze every last drop of value out of every asset.
- Refurbishment and Resale: Devices that Apple won't touch but are still perfectly good can be professionally refurbished and sold on the secondary market.
- Component Harvesting: Even broken devices have gold inside. Valuable parts like memory, processors, and screens can be harvested and sold individually.
- Revenue Sharing Models: Many ITAD partners, including us, offer revenue-sharing deals. That means your company gets a cut of the profits from the resale of your old equipment.
Suddenly, what was going to be a disposal cost becomes a brand new revenue stream. It's a direct, positive impact on your company's finances. You can get a much better idea of the whole journey by reading up on what happens to recycled electronics in a professional ITAD process.
A Broader Strategy for Asset Recovery
Getting the most back means looking at all your retired assets, not just the Macs and iPhones. Most businesses have closets full of other electronics and supplies that still have some cash value. Think beyond just recycling and explore other options, like dedicated programs for selling unused toner cartridges and other surplus office gear.
At the end of the day, a strategic approach to ITAD is about more than just getting rid of old stuff. It’s about lining up your security needs with your financial goals and environmental principles. When you pick a partner who can unlock the hidden value in your retired Apple devices, you're turning a necessary task into a smart, sustainable, and profitable business decision.
Choosing the Right E-Waste Partner for Your Business
So, you've decided it's time to retire your company's old Apple devices. That’s the easy part. The final, most critical step is picking the right partner to handle the job. While Apple’s own recycling program looks convenient on the surface, businesses often find it leaves major gaps in security, compliance, and logistics.
Making the right choice here isn't just about getting rid of old gear; it's about protecting your organization from risk and actually hitting those sustainability goals you've set. Think of it like this: you wouldn't DIY a major office renovation. You'd hire a licensed contractor with the right tools and a proven track record. The same logic applies here.
Your Vetting Checklist for ITAD Providers
When you start looking at potential partners, especially here in the Metro Atlanta area, don't let price be the only thing you look at. A solid vetting process puts security and compliance front and center. Use this checklist to ask the tough questions and find a provider who’s actually ready for business-level needs.
-
Verify Their Certifications: This is your first and most important checkpoint. Look for top-tier industry certifications like R2 (Responsible Recycling) or e-Stewards. These aren’t just fancy badges; they are proof that the provider meets the highest standards for data security, environmental safety, and worker protection. No certs? Move on.
-
Confirm Data Destruction Capabilities: Get specific. Ask them how they destroy data. Do they use methods compliant with DoD 5220.22-M or NIST 800-88 standards? Can they bring a shredder to your office for on-site physical destruction? A real pro will be completely transparent about their methods and have the paperwork to back it up.
-
Review Their Documentation Process: A handshake deal is a recipe for disaster. Your partner must provide a complete, auditable paper trail for every single device. That means a serialized inventory list, chain of custody records showing who handled what and when, and legally defensible Certificates of Data Destruction.
Aligning with Security and Sustainability
Choosing a certified partner does more than just tick a box; it reinforces your company's commitment to doing the right thing, just like the big players. Apple's own reports show the massive impact of responsible recycling. The company has cut its total emissions by over 60% since 2015, and using recycled materials alone avoided 6.2 million metric tons of CO2e.
When you choose an ITAD partner with proven credentials, you're not just handing off a task. You're building a secure, compliant, and environmentally responsible process right into your business operations. It’s a strategic move that protects your data, keeps you on the right side of regulations, and boosts your reputation.
Ultimately, you need a partner who gets the unique challenges of business ITAD. For companies in Metro Atlanta, a local, certified electronic waste company can offer the hands-on service and verified security that a mail-in program just can't match. Making that choice is the difference between turning your old equipment into a success story and leaving it as a lingering liability.
Your Top Questions About Business E-Waste Answered
When you’re staring down a pile of old office computers, a lot of questions pop up. Here are some quick, straightforward answers to help your business handle its old Apple gear the right way.
What's the Real Difference Between Wiping and Destroying a Hard Drive?
Think of it like this: data wiping is like using software to scribble over every single word in a notebook until it's unreadable. For most situations, that works. But physical destruction? That’s putting the notebook through an industrial shredder until it’s just a pile of confetti. There's 100% certainty nothing is coming back from that.
If your business handles sensitive client data, financial records, or anything you wouldn’t want on the front page of the news, physical destruction is the only way to be absolutely sure.
Can't My Business Just Use Apple’s Standard Recycling Program?
That’s a common question, but the short answer is no. The free recycle program Apple offers is great for you and me dropping off an old iPhone, but it’s built for individual consumers, not for the demands of a business.
It’s completely missing the critical pieces an organization needs:
- Bulk Logistics: It’s not set up to handle a whole office worth of MacBooks, iMacs, and iPads in one go.
- Certified Data Destruction: You won't get any official certificates proving that your company's sensitive data was properly destroyed.
- Compliance Paperwork: Forget about getting the auditable reports you need to prove you’re compliant with regulations like HIPAA or PCI DSS.
Trying to use the consumer program for business assets leaves you with massive security risks and serious compliance headaches.
How Much Is This Going to Cost Us?
It’s probably a lot less than you think. In fact, it might not cost you anything at all. When you work with a certified ITAD partner, they look at the resale value of your retired Apple equipment.
If those devices can be refurbished and sold, that value can be shared back with you. The whole process can end up being cost-neutral or even generate a check for your company, turning an expense into revenue.
This flips the script entirely. Instead of paying to get rid of old tech, you’re making a smart financial move that maximizes the return on your original investment.
Ready to build a secure, profitable, and compliant plan for your old IT assets? Montclair Crew Recycling specializes in certified data destruction, secure logistics, and getting the most value back for Metro Atlanta businesses. Protect your data and your budget. Get a free quote today by visiting us at https://www.montclaircrew.com.
