Properly retiring a server isn't as simple as yanking a power cord. You need a solid, structured process that covers planning, data backup, secure data destruction, and finally, eco-friendly hardware disposal. Just unplugging a server and shoving it in a closet is a massive risk—one that can easily spiral into data breaches, serious compliance violations, and unexpected operational downtime.
Why You Cannot Just Unplug an Old Server
Thinking about just pulling the plug on that old server humming away in the rack? It’s a tempting shortcut, I get it. But the reality is far more complex. The act to decommission a server is not a simple IT cleanup task; it's a critical business function with serious security, financial, and legal implications. Rushing the process without a plan is like leaving the front door of your office wide open after hours—it just invites trouble.
The fallout from a botched decommissioning can be severe. Imagine an old server packed with years of sensitive customer data or financial records being tossed out with the regular e-waste. If that data falls into the wrong hands, you’re looking at a catastrophic mess that could lead to huge financial losses and permanently damage your company's reputation.
This simple diagram shows the direct line from a hasty unplug to major business consequences.
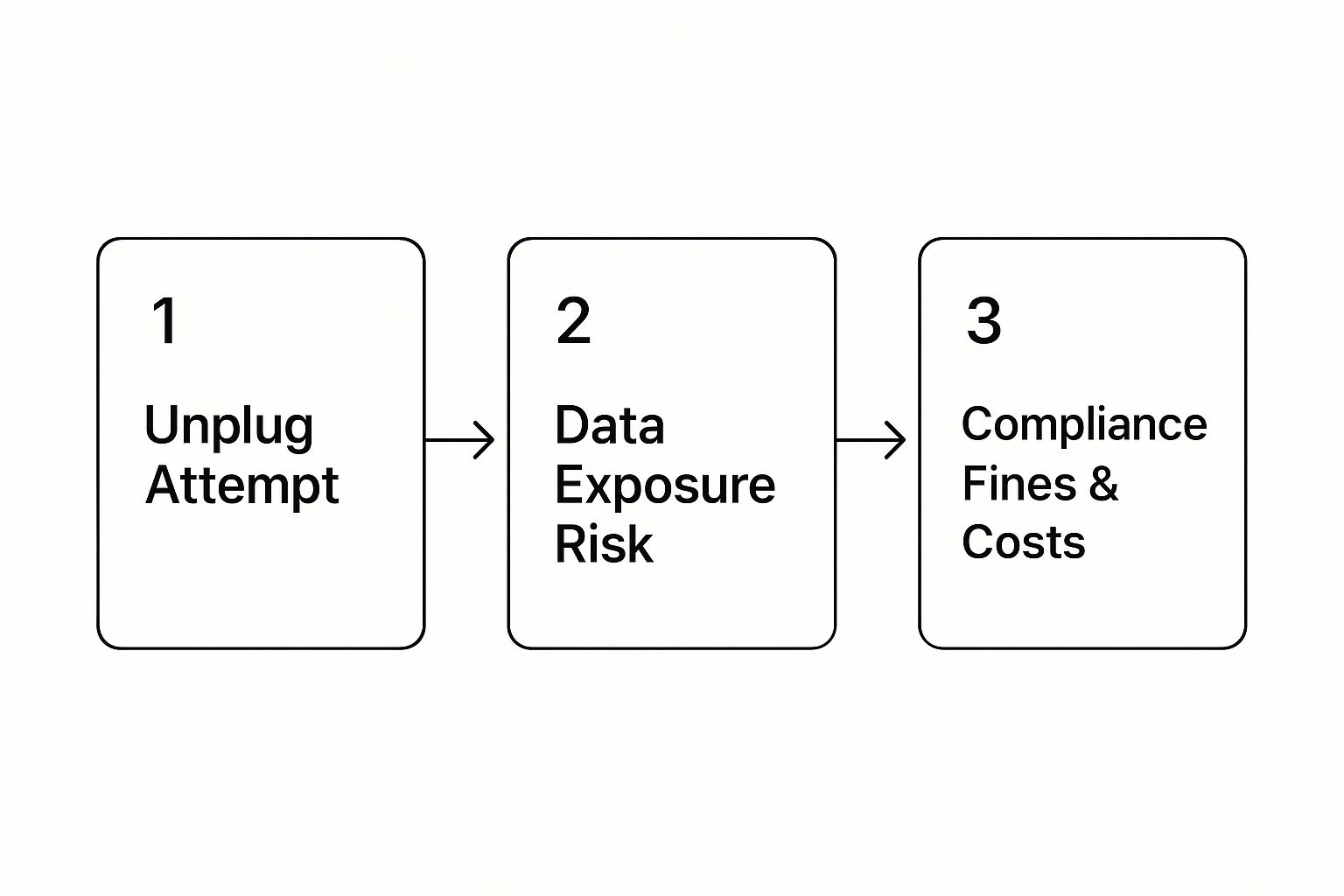
As you can see, what starts as a seemingly harmless action quickly escalates into data exposure, which in turn leads to very real, very tangible penalties.
The Real Risks of Ghost Hardware
Beyond the immediate threat of a data breach, unplugging a server without a formal process creates what we call "ghost hardware"—devices that are physically present but completely off the books in your inventory. These forgotten assets hide several dangers right under your nose:
- Compliance Violations: Regulations like GDPR and HIPAA have iron-clad rules for data handling and destruction. If you can't prove you securely wiped a server's data, you could be facing fines that easily run into the millions of dollars.
- Security Vulnerabilities: An unplugged server might be forgotten, but if it ever gets accidentally powered back on without being patched, it becomes an instant, unsecured entry point for attackers on your network.
- Wasted Resources: Every server, even an idle one, sucks up power and takes up valuable rack space. A proper decommissioning process reclaims these resources, cutting operational costs and freeing up that precious data center real estate.
A server isn’t truly "gone" until its data is verifiably destroyed and its existence is wiped from all asset management systems. Neglecting this creates a ticking time bomb for your security and compliance teams.
Ultimately, a structured approach is non-negotiable. It turns a technical chore into a strategic practice that protects your business from top to bottom. The process ensures every dependency is accounted for, every byte of data is secured, and every piece of hardware is handled responsibly. For anyone managing multiple assets, understanding the nuances of professional IT equipment removal is absolutely essential for keeping your operations secure and intact.
Building Your Decommissioning Game Plan
A successful server decommissioning is 90% planning and 10% execution. I’ve seen it time and time again—rushing this stage is the fastest way to cause an unexpected, business-halting outage. Before you even think about touching a single cable, you need a solid blueprint.
This isn’t just about pulling the plug on a single server; it’s about understanding the entire web of services connected to it.
Start by mapping out every single dependency. Your first job is to identify every application, database, and scheduled task that relies on the server you're retiring. Think of it like creating a relationship map for your infrastructure. Does it host a critical database for your finance app? Does a legacy piece of software ping it for authentication every hour? These are the crucial details you have to uncover before you do anything else.

Assembling Your Decommissioning Team
Let’s be clear: this is not a solo mission. Pulling together a small, cross-functional team is non-negotiable if you want this to go smoothly. Your roster needs key people who can give you the complete picture of the server's role in the organization.
Your ideal team should include:
- System Administrator: This is the person who knows the server's configuration, network connections, and quirks inside and out. They're your technical lead.
- Application Owner(s): The business or IT lead responsible for the software running on the server. They are essential for confirming when a service can be safely shut down and moved.
- Security Expert: You need someone to oversee the data sanitization process and make sure every action is compliant with regulations like GDPR, HIPAA, or whatever else applies to your industry.
This collaborative approach is your best defense against those dreaded, "Hey, I didn't know you were turning that off!" emails that can derail the entire project. Each person brings a unique perspective that helps spot risks you might otherwise miss. Our guide on https://www.montclaircrew.com/it-equipment-decommission/ procedures offers more detailed insights into managing this whole process.
Defining Timelines and Communication
With your team in place, it's time to get a clear timeline on the board. Map out specific milestones and assign ownership for each task. Who is responsible for the final data backup verification? Who's coordinating with the application owner for user acceptance testing on the new system? Get it all documented.
The rapid pace of technology means organizations are constantly retiring old hardware. In fact, a staggering 42% of organizations refresh their data center servers every two to three years. This makes having a repeatable, documented decommissioning plan more critical than ever.
Finally, create a communication plan. This isn't just a courtesy; it's a critical project document. It should outline how and when you'll notify stakeholders of progress, planned outages, and the final shutdown. A truly robust game plan often involves creating clear Standard Operating Procedures (SOPs) to ensure every step is followed precisely, from data destruction all the way to hardware disposal.
This blueprint is what transforms a potentially chaotic process into a predictable, controlled, and successful project.
Safeguarding Your Data During Backup and Migration
Let's be clear: the data sitting on the server you're about to decommission is your most valuable asset. Protecting it during the backup and migration isn't just a technical checkbox—it's the absolute foundation of business continuity. One missed database or a single corrupted file can derail the entire project, creating a recovery nightmare you don't have time for.
This isn't a simple copy-and-paste job. A solid strategy is required to make sure every last byte is moved securely, completely, and with its integrity fully intact. The first big decision is figuring out the right backup approach for your specific situation.

Choosing Your Backup Strategy
Most of the time, you'll be looking at either a full or an incremental backup. A full backup is exactly what it sounds like—it copies everything. This makes restoring the data straightforward but eats up more time and storage space. An incremental backup, on the other hand, only saves what's changed since the last backup. It's much faster, but restoring from it can be more complicated.
So, which one do you choose?
- Go with a Full Backup when: You have a decent maintenance window and need the simplest, most foolproof restoration possible. This is the go-to for servers with mostly static data or when you're moving to a completely new system.
- Opt for an Incremental Backup when: Downtime is your biggest enemy. You can run a full backup over the weekend, then perform quick incremental backups right before you make the final switch, keeping the service interruption to a bare minimum.
No matter which path you take, verifying that the data is sound is non-negotiable. This means going deeper than just checking for "copy complete" messages.
The real test of a backup isn't if it was created successfully, but if it can be restored perfectly. Always perform a test restoration to a non-production environment before you decommission a server.
Verifying Data Integrity Post-Migration
Once your data is sitting on its new home, you need to prove it's all there and uncorrupted. Checking file counts and folder sizes is a good first step, but it won’t catch subtle data corruption. For that, you need something more robust, like checksums.
By generating a hash (think MD5 or SHA-256) for critical files or database dumps on both the old and new servers, you can mathematically prove they are identical. If the hashes match, your transfer was a success. If they don't, you've caught a problem early and can re-copy the affected data before it impacts your operations. Exploring different essential data backup solutions can also add extra layers of security to your process.
For databases, this involves running integrity checks and querying record counts to confirm nothing was lost in transit. Once you're 100% confident in the migration, it's time to make sure the old data is gone for good. You can find more information on the best methods for secure data erasure in our other guides.
Executing the Final Shutdown and Data Destruction
You've migrated and double-checked your data. Now it’s time to pull the plug. This is that point of no return where the old server is finally taken offline for good. But it’s not as simple as flipping a switch. You need a graceful shutdown, which means systematically stopping all services before cutting the power. This one last step prevents any chance of data corruption right at the finish line.
Once the server is offline, your mission changes completely. You're no longer preserving data; you're annihilating it. The absolute priority is making sure not a single byte of sensitive information can ever be pulled from those old hard drives. This is how you close the door on a future data breach from discarded equipment.
Choosing Your Data Destruction Method
When you decommission a server, getting rid of the data isn’t a suggestion—it's a critical security mandate. You’ve got a few industry-accepted ways to do this, and the right choice depends on your security needs, budget, and the kind of data you're dealing with.
Here are the three main ways to get the job done:
- Software-Based Wiping: Think of this as digital bleach. Specialized software overwrites every inch of the hard drive with random junk data, usually in multiple passes. This makes the original information practically impossible to get back.
- Degaussing: This method uses an incredibly powerful magnet to scramble the magnetic coating on a hard drive platter. It’s an instant and permanent kill switch for data, but it also fries the drive, making it totally unusable afterward.
- Physical Shredding: This is the most foolproof option. The hard drives are literally torn apart and shredded into tiny bits of metal. There’s no coming back from that.
Sticking to a recognized standard is the only way to prove you did this right. The NIST 800-88 Guidelines for Media Sanitization is the gold standard, providing a clear framework for clearing, purging, and destroying data. Following it is how you prove due diligence.
The Importance of Certified Destruction
Wiping or shredding the drives yourself is one thing, but proving it is another. This is where a Certificate of Data Destruction (CoDD) becomes your most important document. It’s a formal record from a certified IT Asset Disposition (ITAD) partner that confirms the data was destroyed according to compliance standards.
A proper CoDD will always include details like:
- Serial numbers of every single drive destroyed.
- The exact destruction method used (shredding, degaussing, etc.).
- The date and location where the destruction happened.
- A formal statement of compliance with regulations like HIPAA or GDPR.
This certificate is more than just paperwork. It's your legal, auditable proof that you took your data protection duties seriously. If an auditor comes knocking or a security investigation kicks off, that CoDD shows you took every necessary step to prevent a breach from your retired gear.
To get a better handle on this, it's worth learning what data sanitization entails and why it's so non-negotiable. Ultimately, certified destruction is the final lock on the door for your server decommissioning project.
Handling the Hardware and Final Asset Disposition
Okay, the server is offline and its data is nothing more than digital dust. Now you're left with the physical box. This is the last leg of the race, but it’s just as important as the first. This isn't just about clearing rack space; it's about properly closing the loop on your asset management and meeting your environmental responsibilities.
First things first: get that server safely out of the rack. Before you even think about touching a screwdriver, do a final check. Are all power cables disconnected, including any redundant PSUs? Are the network cables unplugged from the server itself? Once you're absolutely sure it's an island, you can go ahead and carefully slide it out.

Don't Forget the Paperwork
I can't stress this enough: update your documentation the moment the server is out. People skip this step all the time, and it always comes back to bite them later.
Here’s a quick checklist to run through:
- Asset Management System: Go in and mark the server's status as "decommissioned" or "disposed." Add the date and how you got rid of it (e.g., recycled by ABC Corp, resold).
- Network Diagrams: Erase the server from your network maps. You don't want a new engineer trying to troubleshoot a connection to a machine that doesn't exist.
- CMDB: Any entries in your Configuration Management Database that referenced this server need to be updated to show it's gone.
Neglecting your records creates "documentation ghosts." These phantoms haunt you during future audits, troubleshooting sessions, and expansion planning. It’s a five-minute task that prevents hours of headaches down the road.
Choosing a Smart ITAD Strategy
So, what do you do with the hunk of metal you just pulled out? Tossing it in the dumpster is a huge no-go. Responsible IT Asset Disposition (ITAD) isn't just good practice; it's often a legal requirement. The idea is to squeeze any remaining value out of the hardware while being kind to the planet.
You've basically got three paths to choose from:
- Remarket: If the server or its parts (think RAM, CPUs, or high-end network cards) aren't ancient, they might be worth something. A good ITAD partner can test the hardware and handle the entire resale process for you.
- Donate: Got older gear that still works? Non-profits, schools, and local community centers would probably love to have it. Not only does this help a good cause, but you might also be able to get a tax deduction.
- Recycle: For anything that's truly at the end of its life, certified e-waste recycling is the only way to go.
When you're picking a recycler, make sure they have certifications like R2 (Responsible Recycling) or e-Stewards. These credentials are your guarantee that they handle data security, environmental safety, and worker protection by the book.
The market for these services is blowing up, especially in North America and Europe where environmental laws are tight. But we're seeing huge growth in places like the Asia Pacific region as sustainable IT becomes the global standard.
This final step is what makes the entire process complete—secure, compliant, and environmentally sound from start to finish. For a deeper dive into disposing of various types of electronics, check out our guide on how to dispose of old computers safely.
Common Server Decommissioning Questions Answered
Even the best-laid plans run into hiccups. When you’re taking a server offline for good, unique questions and weird situations are just part of the job. Let’s tackle some of the most common ones I hear from teams on the ground.
How Long Does It Take to Decommission a Server?
This is the classic "it depends" answer, but it's the truth. The timeline can swing from a single weekend to several months. A simple, standalone file server with just a handful of users? You could probably knock that out in a day or two.
But a core application server that’s tangled up in multiple business systems is a different beast entirely. We're talking months of careful planning, a phased migration strategy, and extensive testing with every user group to make sure nothing breaks. The schedule always comes down to the server’s complexity, how critical its services are, and the sheer volume of data you need to migrate safely.
What Is the Most Common Decommissioning Mistake?
The biggest and most painful mistake, by far, is missing a dependency. It’s a story as old as IT: a team shuts down a server, gives each other high-fives, and an hour later, the help desk phones start ringing off the hook. Turns out, a forgotten but critical script or a legacy app was still quietly relying on it, and now you have an outage on your hands.
There's no shortcut here. The only way to avoid this mess is through exhaustive discovery and clear, constant communication with every single department. It’s tedious work, but it’s the single most important step people try to skip.
When Should I Hire a Professional Service?
If you have an experienced internal IT crew, they can absolutely handle decommissioning a single, low-risk server. But for certain situations, bringing in a professional IT Asset Disposition (ITAD) vendor isn't just a good idea—it's essential.
You should seriously consider hiring experts for:
- Large-scale projects: Taking down multiple servers or clearing out an entire data center requires logistical precision. ITAD specialists live and breathe this stuff.
- Servers with sensitive data: If that machine held customer PII, financial records, or patient health information, using a certified vendor for data destruction is non-negotiable for compliance.
- Regulatory requirements: Professionals provide certified data destruction and a full, auditable chain of custody. This paperwork is your proof that you met all your legal and industry obligations.
There's a reason the global data center decommissioning market is booming. It was valued at USD 89.35 billion in 2024 and is expected to climb as more businesses focus on secure and sustainable IT. If you want to dig into the numbers, you can explore more insights about the data center decommissioning market.
What Is a Certificate of Data Destruction?
A Certificate of Data Destruction (CoDD) is the official document that proves the data on a device was permanently and securely destroyed. Your ITAD partner provides this once their work is done.
Think of it as the final receipt for your server's end-of-life journey. This document is your get-out-of-jail-free card during a compliance audit, showing you handled sensitive data the right way.
It will always include critical details like:
- The unique serial number of every single hard drive destroyed.
- The exact destruction method used (like shredding or degaussing).
- The date and location where the destruction took place.
At Montclair Crew Recycling, we specialize in secure, compliant, and eco-friendly IT asset disposition for businesses all over the Atlanta area. We take the complexity out of the process—handling everything from on-site removal and certified data destruction to responsible recycling. We make sure your server decommissioning project is managed professionally from start to finish. Learn how we can help protect your data and manage your retired IT assets at https://www.montclaircrew.com.
